


By Dr Nur Izura Udzir and Adibah Ahmad.
Science as a field of knowledge has enabled man to produce new findings that create technology. One of the positive impacts of science is in communication technology, which drives globalization. Globalization has been a buzz word for the past three decades. Nobel Laureate Joseph Stiglitz defines globalization as “…the closer integration of the countries and peoples of the world which has been brought about by the enormous reduction of costs of transportation and communication, and the breaking down of artificial barriers to the flows of goods, services, capital, knowledge, and (to a lesser extent) people across borders.” [1]. There are four basic aspects of globalization: (a) trade and transactions, (b) capital and investment movements, (c) migration and movement of people, and (d) the dissemination of knowledge [2]. Besides economics, domestic and international politics, information and communication technology (ICT) revolution is one of the factors that have contributed to globalization [3].
The escalation of the Internet and mobile communication usage facilitates dissemination of information, and thus contributes to globalization. The vast benefits of globalization through ICT are undeniable – in terms of economy, administration and governance, socio-cultural, as well as education. Unfortunately, the ‘openness’ of globalization also opens doors for negative influences, and the challenges posed by this globalization are not to be ignored.
BENEFITS OF GLOBALIZATION THROUGH ICT
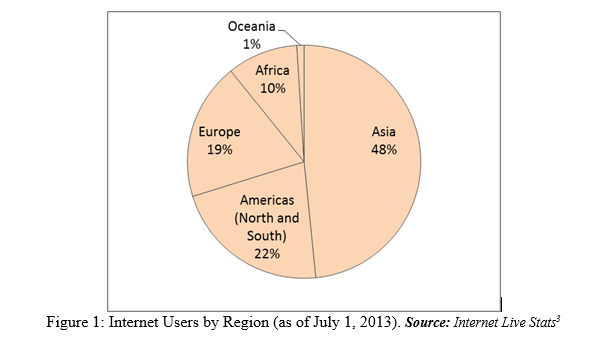
The power of the Internet, for example, which connects users around the world, has seen a steady increase in its usage. There are now three billion Internet users worldwide, i.e. 40% of world population, as compared to a mere 1% in 1995. Figure 1 shows the Internet users in the five regions of the world.
The growing impact of ICT on globalization provides more flexibility, more efficiency, and speed in many aspects of life. In terms of economy, globalization through ICT creates a new industry, provides more jobs, improve businesses, and opens opportunities, as it facilitates communication, reduces costs of transactions, connecting industries (enables more extensive networking and co-operations among industries). ICT now is a must in the business world in order for businesses to persist as the competition is very high. As businesses are relying more on ICT, their performances are strongly affected by ICT.
The impact of ICT in administration can be seen through e-governments and automated systems. ICT can be used to enhance the access and delivery of government services to benefit citizens, creating a more efficient and effective governance, as well as a more transparent government.
From the socio-cultural perspective, ICT connects and reconnects people (families, friends, etc.) through social media, or social networking services, for example. This somehow creates another kind of society, i.e. cyber society. From another aspect, globalization through ICT also aids in increasing the literacy (and IT literacy) rate in developing nations as communities are more exposed to technology and information. Even community services and activities, including da’wah can be facilitated using ICT.
In terms of education, ICT undoubtedly plays an important role in improving the quality of education, opening a whole new dimension of learning and improving the teaching and learning process, for better learning experiences.
Globalization through ICT is not limited to the use of computer networks, but also includes mobile devices and mobile networks. With mobile devices, it is akin to carrying ‘everything in your pocket’ – your bank, address book, the Holy Qur’an, entertainment, edutainments, dictionary, etc.
[3] Elaboration of data by International Telecommunication Union (ITU) and United Nations Population Division
CHALLENGES OF GLOBALIZATION THROUGH ICT
There is no doubt that the advancement of ICT has brought both opportunities and challenges to nations in their efforts to ensure socio-economic development and improve public governance. In the wake of globalization, societies have no choice but to take advantage of the opportunities and face the challenges.
Similar to its benefits, the challenges of the globalization through ICT are seen in the business world, politics, and socio-cultural. Among the main challenges are the free-flow of information which can be rather difficult to control, opening various possibilities for misuse and abuse of the technology for malicious intent. Various attacks can easily be launched against businesses and governments via the network, such as denial of service (DoS), mailbombs, hack threats, and web defacement. Socially inter-connected users are more susceptible to privacy risks as these social websites can be used as a tool to harvest information from unsuspecting targets. This also includes personal data risk from mobile apps, which will continue to rise with the continuing adoption of emerging apps for personal and business communication, particularly for socially engineered scams and data exfiltration attempts [4].
EFFECTS OF GLOBALIZATION ON FAMILY AND SOCIETY
There seems to be no limit to the effects of globalization. The effects can be seen not only in economics and politics, but also in socio-cultural aspects, affecting family and society. Over the years, the influence of globalization through ICT, with the vast amount of information available to anyone, has changed the way people think, or perceive things, and the values of society, which are inter-related with family harmony.
Over-exposure to uncontrolled and unfiltered information may lead to social problems. Uncensored and indecent videos which contain inappropriate as well as violent elements can be a negative influence to impressionable youths. For example, children and youth can learn many things from the Internet, such as learn how to perform solat, wudhu (ablution), learn to read the Qur’an, tajwid, etc. On the other hand, they can also easily learn immoral, even unlawful things – such as how to make explosives, how to commit fraud, scams techniques, auto theft, and so on. Nevertheless, with proper guidance, and strict monitoring, the technology can be used in various positive ways.
Digital Children v. Analog Parents
Statistics show the drastic increase in Internet users since the 1990s. For the past decade, the majority of the users are young generations, i.e. Generation Y (those born between 1977-1994), Generation Z (born between 1995-2012), and partly Generation X (born between 1966-1976). The Generation Z, whom are our children today, use digital communications to interact with their peers. Regrettably, many parents lack the skill and ability, or are uncomfortable to use this type of communication, which may be attributed to their unfamiliarity with the perceived complexity of these devices, or their mistrust and scepticism towards these technologies. They are more comfortable to use ‘analog signals’ or conventional methods in conveying information, giving advice, face-to-face conversation and discussions, or at the very least communicate over the telephone. Most parents still insist to communicate in a setting where the children should ‘listen’ to what they are saying.
Unfortunately, the conventional approach of face-to-face ‘parents talk, children listen’ is no longer effective in most cases nowadays. Making our children listen to us can be one of the most challenging tasks. So how parents communicate with their children today is a new challenge and a new skill that needs to be mastered to ensure effective parenting.
Risks through ‘Open’ Friendship
Through online communication, such as social media, email, online chat services, people can be connected to other people around the globe. Children have the opportunity to make friends from all over the world and from various background and religious beliefs. They might be attracted to the lifestyle which does not conform to syari’at, e.g. the way they dress, the way they talk, and the way they behave. It may also affect their understanding on concepts and principles related to love, marriage, sexual relationship, abstinence, and homosexuality. Even worse, there are many cases where children or teenagers are exposed to relationships that may lure and seduce them to perform sexual acts, or deceive them into sexual abuse or prostitutions. Some may also be vulnerable to scams which may involve them in drug trafficking (as drug mules) or human trafficking.
Financial Impact
The explosive effect of online marketing and online shopping has promoted luxurious lifestyle, which attracts and entices susceptible users. Online shopping habit can become an addiction to adults and youth alike. Users may be tempted to buy stuffs online, due to its convenience and, with the use of credit cards, they can be oblivious to the amount of money they have spent, and they normally overspent beyond their means. The burden of credits, loans, and mortgages may affect family stability. Teenagers too are easily influenced by advertisements, the luxurious lifestyle portrayed in the media and the Internet. We have heard of children and teenagers purchased goods using their parents’ credit cards, with telephone and Internet bill exceeding the usual limit.
Da’wah and Risks to Beliefs
For the past decade, in the wake of Islamophobia, awareness and interest towards Islam has increased, and with the borderless world made possible by the globalization, da’wah and the teachings of Islam have spread through ICT, among other mediums. Many websites have promoted Islam to the world, dispensing valuable information to the curious. However, for people searching for more knowledge on religion and Islam, there is a potential of being exposed to wrong information about Islam, and this may create conflicts in their beliefs and within themselves. Naïve and curious teenagers may be misled to believe untrusted and untruthful information, and thus, without proper guidance, may deviate from the true teachings of Islam.
Cyber Threats
Over the past 20 years attackers have increased in intensity and frequency, they are more creative in their methods, and attacking tools have evolved. Cyber-crime is one of the fastest growing areas of crime, such as identity theft and the distribution of child sexual abuse images. Many new threats are emerging, which can be categorized as intrusions, malicious codes, denial of service (DoS), mailbombs, phishing/vishing/smishing, spamming, hack threat, website defacement, spyware, and more. There are also cyber threats that may affect family and society, such as scams, fraud, cyberstalking, cyberbaiting, cyberflirting, social engineering and even cyber-terrorism.
Scams are techniques used to dupe victims with fake messages, such as rewards, in order to swindle their money. The attackers would send a message, either via email, telephone, or text messages, falsely leading the target (victim) to believe that he has won some reward, and in order to claim the reward, the target must deposit some amount of money. Scams such as phishing (through email), vishing (voice, i.e. via telephone), and smishing (using SMS/text messages) are rampant. On top of these, there are also love scams, drug mule scams, and other more serious scams that can affect the family institution and society.
Fraud is a criminal activity using computer systems to deceive and scam people, government, and companies, more often involving money. The illegal activity may include methods like phishing, social engineering, DoS, etc. to commit identity theft, bank fraud, extortion, and steal classified information. Identity-related crime, i.e. identity theft or identity fraud has become a significant problem worldwide, which may be in the form of utilities fraud, bank fraud, employment fraud and credit card fraud [5].
Cyberbullying involves the act of harassment, such as sending unkind or hostile messages, rumours and embarrassing pictures, videos, websites, or fake profiles through text messages, emails, social networking sites.
Cyberstalking, if mildly defined, refers to the use of the Internet to ‘follow’ a person with intent without that person’s consent. However, it may include making false accusations or statements of fact (as in defamation), monitoring, making threats, identity theft, damage to data or equipment, solicitation of minors for sex, gathering information that may be used to harass [6]. Cyberstalking is a form of cyberbullying.
Cyberbaiting is on the rise. In this form of threat students provoke a teacher into having an outburst or a breakdown, which will be filmed by the students on cell phones to be posted online, causing further shame or trouble for the teacher or school. Recently, 21% of teachers experienced cyberbaiting, or knew of a colleague who has been cyberbaited [7]. Cyberbaiting is also a form of cyberbullying.
Cyberflirting is related to cyberbaiting. First emerged in 2008, the perpetrator flirted with their victims and persuaded them into posing (some are indecent poses) for them via webcams, and later blackmail the victims by threatening to post the photos on the Internet if the culprit is not paid.
Cyber-terrorism refers to terrorist activities carried out via the use of Internet using computer viruses and hacking techniques, including acts of deliberate, large-scale disruption of computer networks. This can be a direct threat to nations and countries.
Social engineering involves manipulating people into performing actions or disclosing confidential information, which can be used in privacy attacks and identity theft. Most social engineering techniques are designed to appear innocuous so as not to alert unsuspecting victims, e.g. online surveys or quizzes.
FAMILY SAFETY ON SOCIAL NETWORKING SERVICES
The way we use the Internet has changed significantly over the past few years. The fast development of the Internet results in the development of social networking services a.k.a. social media, such as Facebook [8], MySpace [9], Twitter [10], and Orkut [11]. Less than a decade ago, social networking sites were a strange notion. Now, there are over 1.35 billion monthly active users of Facebook alone[4]. The rising popularity of these websites has witnessed the overwhelming increase in the use of their services, inadvertently providing a fertile ground for social engineers to harvest information from unwary targets.
Social media appeals to users, especially the younger generations as it interconnects people around the globe – they can have friends from all over the world, connect and reconnect with new and old friends, share their experiences, photos, thoughts, feelings, and many things online. However, parents will face a difficult challenge to control what their children share and with whom they share it. There is the threat of oversharing – giving out too much information about themselves, which may be used against them.
Privacy issue in social networking is a hot topic. Some social networking sites do not limit the sharing of user data with a third party such as advertisers who may use personal data and information obtained through cookies to achieve their targets. Most user naïvely assume the social networking services will not disclose any private information to others. Furthermore, privacy policy and terms of used are incomprehensible by most users.
According to Brenner [12], the seven ‘deadly sins’ committed by most Internet users that can result in grave consequences are:
The seemingly innocuous and harmless information divulged by users can be used to extract and harvest information for malicious or even criminal purposes.
[4] Facebook statistics as of 28 Oct 2014
Social Engineering on Social Networking Services
Social engineering is a common tool for privacy attacks and identity theft. With the increasing popularity of social networking services, users are more susceptible to privacy risks as these websites can be used as a tool to harvest information from unsuspecting targets. In their enthusiasm to get connected, most users may not be aware of how much personal information they are exposing, or perhaps this may seem inconsequential to the user, thinking that it will not bring any harm to them. In their naiveté they are unaware that this information combined with other information disclosed from other sources can be used by a social engineer to profile the user which can be used against them.
For example, it can be surprising how much information can be collected from seemingly harmless online quizzes designed for social network websites, and how the harvested information can be misused to initiate different attacks against users’ private information [13]. Information taken from each user can be used to develop the victim’s profile, which might then be used against them, such as spear phishing, i.e. to entice users to download malwares such as backdoors and Trojans, or for further information harvesting. In addition, an attacker can impersonate a person after gathering bits and pieces of information from various websites to build a profile of the victim, or worse, can even attempt a scam or physical attack on the victim, such as break-in, staking, or rape, based on the profile they have created, and pattern learned.
MANAGING THE RISK
The growing globalization through ICT has created a new threat and challenges to family and society. Although globalization through ICT has multiple benefits to family and society, it also has security risks that need to be managed thoroughly for a more secure technology usage.
One of the best defenses against cyber threats is security awareness. Every user should be educated on the threat and risks posed by technology, Internet, and social networking, and how these threats and risks can be prevented with some simple countermeasures [13], such as:
In general, users can take simple measures to protect themselves against cyber threats by being discreet, skeptical, thoughtful, professional, and wary while using the Internet, especially social networking services.
CONCLUSIONS
With the growing popularity of the Internet and social networking, people are being connected globally, regardless of their location. Globalization through ICT has offered many advantages – it opens opportunities for business and economic growth, a more efficient governance of governments, and vast amount of knowledge which are easily accessible, leading to more effective learning experience to enhance education.
On the other hand, it also poses many challenges if the usage is not properly managed. Among the challenges are its effects on family institutions, values and society stability and harmony. The largest group likely to be affected by the globalization through ICT are the young generations – in their eagerness and enthusiasm in using the technology they sometimes fail (either forget, or even due to their ignorance) to take the necessary precautions to protect themselves against the risks and threats posed by these usage. Nonetheless, these risks are not exclusive to the young generations, as many mature and ‘sensible’ adults have also fallen prey to the threats. Hence, it is imperative that all users of ICT need to be made aware of the challenges and threats, and how the usage can be managed and controlled, and the risks can be reduced or mitigated, so as to preserve family stability and society harmony.
REFERENCES
Associate Profesor Dr Nur Izura Udzir is Vice President of WADAH (Women Affairs) and Adibah Ahmad is Exco member of WADAH. This paper has been presented at the 2nd International Family Conference 2015, 24-25 January 2015 in Istanbul, Turkey, organized by the Union of NGOs of the Islamic World (UNIW). The authors are grateful to Yousef Bakhdlaghi for his help in translating the article to Arabic.



